Overview
WE HELP YOU PROTECT YOUR WEBSITE
We specialize in protecting your web application through comprehensive web application penetration testing. This process simulates real-world cyberattacks to identify and fix vulnerabilities before they exploit. Web application pentest is key to ensure security of your online presence. At CyberCovert, we deliver expert web application penetration testing to keep your business safe by identifying vulnerabilities and providing actionable insights to strengthen your security posture against data breach.
Value Propositions
Core Benefits
Why proceed for a web application penetration testing?
The Risk
Over 30,000 Websites Hacked Daily
Approximately 30,000 websites are hacked every day globally, often due to vulnerabilities in outdated software, weak passwords, or misconfigurations. These breaches can lead to data theft, defacement, or unauthorized access, affecting businesses of all sizes.
Web Application Penetration Testing is essential to proactively identify and remediate these vulnerabilities before attackers can exploit them. By simulating real-world attack scenarios, organizations can strengthen their web applications’ security posture, protect sensitive data, and maintain customer trust.
Discover More
Gain Visibility into Your Attack Surface Exposure
Discover where you are vulnerable
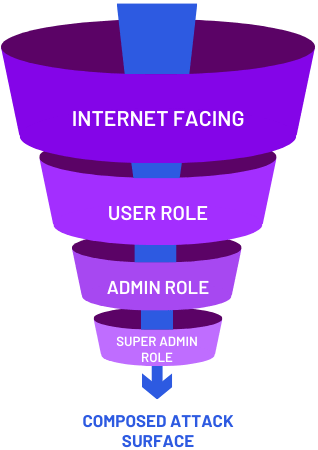
Internet Facing
Public-facing applications and services are primary entry points. These enttry point are often contain misconfigurations, outdated components, and vulnerable functionality.
User Role
Standard user accounts expand the internal attack surface. They reveal internal app function and behaviors, directory structures, and lateral movement opportunities.
Admin Role
Admin interfaces and privileges increase attack depth. These roles expose configuration panels, internal tools, and elevated operations that attackers seek to abuse.
Super Admin Role
Super admin portals expose the deepest layers of the environment. These surfaces allow attackers to manipulate core systems, access sensitive data, and establish long-term control.
The Flow
Our Approach
We blend thorough reconnaissance, precision exploitation, and actionable reporting to fortify your web applications against real‑world threats.
First Step
Engagement Scoping
Every web penetration testing begins with careful planning. This includes defining the scope, setting clear objectives, and understanding the systems to be tested. During this stage, we collect relevant information about the target web application to ensure a focused and effective assessment.

Second Step
Vulnerability Discovery & Exploitation
Once preparation is complete, we analyze the web application for potential weaknesses. Using a combination of automated tools and manual techniques, we identify vulnerabilities and, where appropriate, safely test how they might be exploited. This helps us understand the real-world risks facing the system.


Last Step
Reporting & Remediation
Once the web penetration testing finishes, we deliver a detailed report outlining the findings, their potential impact, their POC, and clear recommendations for fixing them. We also offer support during the remediation process and can retest to ensure that all issues have been properly addressed.


Our security assurance is not based on a one-size-fits-all solution.
What Makes Us Different?
Every security assessment ay CyberCovert follows a thorough process to ensure optimal results.
We combine deep manual expertise with advanced automation to uncover vulnerabilities that others often miss.
We are certified professionals who adhere to industry standards like OWASP and NIST, providing thorough assessments. We deliver clear, actionable reports that prioritize remediation, helping you strengthen your web application’s security effectively. Our testing approach is tailored to your application’s unique architecture, ensuring comprehensive security coverage.

We tailor every solution around your feedback, building trust and lasting loyalty

INDUSTRY CERTIFICATIONS
Our industry recoginzed credentials validate expertise which enhance our performance in delivering you quality work

DIVERSE INDUSTRY EXPERIENCE
From banking to healthcare to payment processors, our cross‑sector insights drive context‑driven security strategies

TAILORED SECURITY SOLUTIONS
Your business, your security—customized solutions for your unique needs

Reach Out Now
30'000 Websites Hacked Daily
We can help you in staying protected.
Get In Touch
Share Your Requirements: CyberCovert Loves To Help You!
At CyberCovert, we understand the unique cybersecurity challenges facing your business, from evolving threat landscapes to stringent compliance demands.
Whether you need a web application penetration test or any other assessment, share your requirements with our certified experts, and we’ll tailor a customized plan to start web application penetration testing for you.

Have Any Doubt?
Frequently Asked Questions
Web application penetration testing is a series of cyber attack performed by skilled security professionals who attempt to exploit vulnerabilities in your web applications—such as SQL injection, cross‑site scripting, or authentication flaws—to assess how an attacker could compromise your data or systems.
With cyber threats constantly evolving, regular pentests help organizations identify and remediate security gaps before adversaries exploit them, reducing the risk of data breaches and ensuring compliance with standards such as PCI DSS Requirement 11.3.
Industry best practices recommend at least annual tests—or more frequently after major updates—so you maintain an up‑to‑date security posture; high‑risk or regulated environments may require quarterly or continuous testing.
Penetration testing typically follow standardized frameworks—such as the OWASP Web Security Testing Guide (WSTG) or the Penetration Testing Execution Standard (PTES)—which outline phases from pre‑engagement and reconnaissance through exploitation and reporting.
Testing focuses on the OWASP Top 10 (e.g., injection, broken authentication, sensitive data exposure) plus business‑logic flaws, misconfigurations, and zero‑day risks, ensuring a broad evaluation of both well‑known and complex attack vectors.
Engagements can be black‑box (no prior access), gray‑box (limited access), or white‑box (full access), each offering different depth and perspectives on your application’s security.
Effective preparation includes defining objectives and compliance requirements, providing network diagrams and authentication details, and securing a testing window to minimize business disruption while maximizing test coverage.
Clients usually supply target URLs, user roles, authentication credentials (for gray‑box or white‑box tests), and any relevant architecture documentation to help pentesters craft realistic attack scenarios.
A standard small‑scale engagement (one application, limited functionality) often takes 1–2 weeks, whereas complex, multi‑application environments may require 4–6 weeks to complete all phases thoroughly.
Costs vary by scope, complexity, and tester’s expertise; small‑scale tests can start around $500, while extensive enterprise assessments often starts from $10,000 price reflects hours invested in discovery, exploitation, and comprehensive reporting.
You’ll get an executive summary for stakeholders, a technical report detailing each finding with risk ratings and remediation guidance, plus proof‑of‑concept evidence (screenshots/logs) and retest options to confirm fixes.
Post‑test, use the report’s prioritized remediation plan to patch vulnerabilities, then schedule retests to verify fixes; integrate lessons learned into your SDLC for continuous security improvement.