Overview
WE HELP YOU PROTECT YOUR WEBSITE
We specialize in protecting your web application through comprehensive web application penetration testing. This process simulates real-world cyberattacks to identify and fix vulnerabilities before they exploit. Web application pentest is key to ensure security of your online presence. At CyberCovert, we deliver expert web application penetration testing to keep your business safe by identifying vulnerabilities and providing actionable insights to strengthen your security posture against data breach.
Value Propositions
Core Benefits
Why proceed for a web application penetration testing?
The Risk
Over 30,000 Websites Hacked Daily
Approximately 30,000 websites are hacked every day globally, often due to vulnerabilities in outdated software, weak passwords, or misconfigurations. These breaches can lead to data theft, defacement, or unauthorized access, affecting businesses of all sizes.
Web Application Penetration Testing is essential to proactively identify and remediate these vulnerabilities before attackers can exploit them. By simulating real-world attack scenarios, organizations can strengthen their web applications’ security posture, protect sensitive data, and maintain customer trust.
Discover More
Gain Visibility into Your Attack Surface Exposure
Discover where you are vulnerable
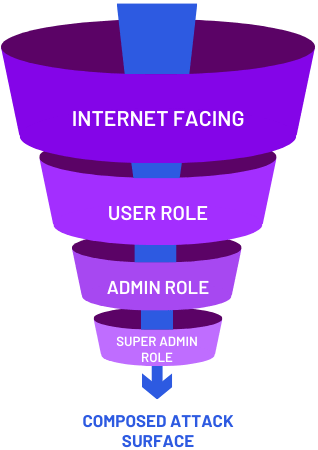
Internet Facing
Public-facing applications and services are primary entry points. These enttry point are often contain misconfigurations, outdated components, and vulnerable functionality.
User Role
Standard user accounts expand the internal attack surface. They reveal internal app function and behaviors, directory structures, and lateral movement opportunities.
Admin Role
Admin interfaces and privileges increase attack depth. These roles expose configuration panels, internal tools, and elevated operations that attackers seek to abuse.
Super Admin Role
Super admin portals expose the deepest layers of the environment. These surfaces allow attackers to manipulate core systems, access sensitive data, and establish long-term control.
The Flow
Our Approach
We blend thorough reconnaissance, precision exploitation, and actionable reporting to fortify your web applications against real‑world threats.
First Step
Engagement Scoping
Every web penetration testing begins with careful planning. This includes defining the scope, setting clear objectives, and understanding the systems to be tested. During this stage, we collect relevant information about the target web application to ensure a focused and effective assessment.

Second Step
Vulnerability Discovery & Exploitation
Once preparation is complete, we analyze the web application for potential weaknesses. Using a combination of automated tools and manual techniques, we identify vulnerabilities and, where appropriate, safely test how they might be exploited. This helps us understand the real-world risks facing the system.


Last Step
Reporting & Remediation
Once the web penetration testing finishes, we deliver a detailed report outlining the findings, their potential impact, their POC, and clear recommendations for fixing them. We also offer support during the remediation process and can retest to ensure that all issues have been properly addressed.


Our security assurance is not based on a one-size-fits-all solution.
What Makes Us Different?
Every security assessment ay CyberCovert follows a thorough process to ensure optimal results.
We combine deep manual expertise with advanced automation to uncover vulnerabilities that others often miss.
We are certified professionals who adhere to industry standards like OWASP and NIST, providing thorough assessments. We deliver clear, actionable reports that prioritize remediation, helping you strengthen your web application’s security effectively. Our testing approach is tailored to your application’s unique architecture, ensuring comprehensive security coverage.

We tailor every solution around your feedback, building trust and lasting loyalty

INDUSTRY CERTIFICATIONS
Our industry recoginzed credentials validate expertise which enhance our performance in delivering you quality work

DIVERSE INDUSTRY EXPERIENCE
From banking to healthcare to payment processors, our cross‑sector insights drive context‑driven security strategies

TAILORED SECURITY SOLUTIONS
Your business, your security—customized solutions for your unique needs

Reach Out Now
30'000 Websites Hacked Daily
We can help you in staying protected.
Get In Touch
Share Your Requirements: CyberCovert Loves To Help You!
At CyberCovert, we understand the unique cybersecurity challenges facing your business, from evolving threat landscapes to stringent compliance demands.
Whether you need a web application penetration test or any other assessment, share your requirements with our certified experts, and we’ll tailor a customized plan to start web application penetration testing for you.

Have Any Doubt?
Frequently Asked Questions
Infrastructure penetration testing is a series of attack against your organization’s IT infrastructure—such as servers, workstations, firewalls, and network devices—to identify and exploit security weaknesses. It helps evaluate your organization’s exposure to real-world attacks and uncovers vulnerabilities that could lead to unauthorized access or data breaches.
Infrastructure penetration testing is crucial for identifying security gaps in your internal and external networks before malicious actors exploit them. It helps protect sensitive data, ensures business continuity, and supports compliance with standards such as ISO 27001, NIST, HIPAA, and PCI DSS.
An infrastructure pentest typically includes vulnerability scanning, manual exploitation, privilege escalation, lateral movement testing, and evaluation of patch management and network segmentation. It may cover both internal (behind the firewall) and external (public-facing) systems depending on the scope.
External infrastructure tests focus on systems exposed to the internet, such as web servers, email gateways, and firewalls. Internal tests simulate an attacker who has breached the perimeter and assesses how far they could go within your internal network environment.
Common infrastructure vulnerabilities include open ports, outdated software, weak or default credentials, misconfigured firewalls, unpatched systems, and poor network segmentation. These weaknesses can allow attackers to move laterally, access sensitive data, or take control of systems.
Infrastructure pentesting follows established methodologies such as the Penetration Testing Execution Standard (PTES), NIST SP 800-115, and OSSTMM. The approach includes planning, reconnaissance, vulnerability identification, exploitation, post-exploitation, and reporting.
The duration depends on the size and complexity of the environment. A basic external test might take 3–5 days, while a comprehensive internal and external engagement for a medium-sized organization may take 2–3 weeks, including the reporting phase.
Costs vary depending on the scope, number of IPs/assets, and testing depth. Prices typically range from $5,000 for small external assessments to over $50,000 for large enterprise-level tests. The investment reflects time, expertise, and depth of testing.
To initiate an infrastructure penetration test, you’ll typically provide a list of in-scope IP addresses, a network diagram, details on user accounts (for internal testing), and timing preferences. This helps define boundaries and expectations for the assessment.
After the test, you’ll receive a comprehensive report including an executive summary, detailed findings, risk ratings, screenshots or logs as proof-of-concept, and prioritized remediation guidance. Many providers also offer a retest to validate that vulnerabilities have been properly fixed.
Social engineering (like phishing or USB drops) can be included as an add-on to infrastructure penetration testing. These assessments test the human element of your security posture and simulate real-world scenarios where attackers exploit employees to gain access.
It is recommended to perform infrastructure penetration testing at least once a year or after any significant changes to your network architecture, security controls, or systems. Regular testing helps ensure that new vulnerabilities are quickly identified and mitigated.