Overview
WE HELP YOU PROTECT YOUR APIs
We specialize in securing your APIs through thorough and targeted API penetration testing. This process simulates real-world attack scenarios to uncover vulnerabilities before they can be exploited. API pentesting is essential to safeguard the integrity of your applications and protect sensitive data exchanged between systems. At CyberCovert, we deliver expert API penetration testing to help your business stay secure by identifying security gaps and providing clear, actionable recommendations to strengthen your API defenses against modern threats.
Value Propositions
Core Benefits
Why proceed for a API penetration testing?
The Risk
57% of Organizations Experienced Multiple API Breaches
57% of organizations reported experiencing an API-related data breach in the past two years, with 73% of these incidents involving three or more breaches. This highlights a systemic failure in existing API defenses and an urgent need for API security solutions.
This escalating threat landscape underscores the critical need for dedicated API penetration testing. Proactively identifying and addressing vulnerabilities, businesses can fortify their defenses against these pervasive attacks.
Discover More
Gain Visibility into Your Attack Surface Exposure
Discover where you are vulnerable
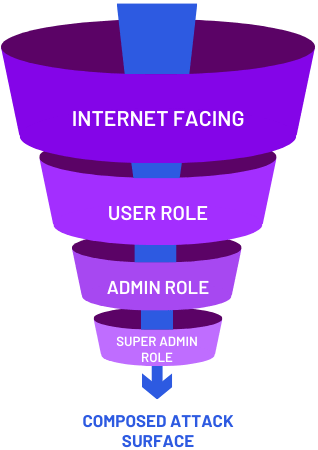
Internet Facing
Public-facing applications and services are primary entry points. These enttry point are often contain misconfigurations, outdated components, and vulnerable functionality.
User Role
Standard user accounts expand the internal attack surface. They reveal internal app function and behaviors, directory structures, and lateral movement opportunities.
Admin Role
Admin interfaces and privileges increase attack depth. These roles expose configuration panels, internal tools, and elevated operations that attackers seek to abuse.
Super Admin Role
Super admin portals expose the deepest layers of the environment. These surfaces allow attackers to manipulate core systems, access sensitive data, and establish long-term control.
The Flow
Our Approach
We blend thorough reconnaissance, precision exploitation, and actionable reporting to fortify your APIs against real‑world threats.
First Step
Engagement Scoping
Every API penetration testing begins with careful planning. This includes defining the scope, setting clear objectives, and understanding the systems to be tested. During this stage, we collect relevant information about the target API to ensure a focused and effective assessment.

Second Step
Vulnerability Discovery & Exploitation
Once preparation is complete, we analyze the API for potential weaknesses. Using a combination of automated tools and manual techniques, we identify vulnerabilities and, where appropriate, safely test how they might be exploited. This helps us understand the real-world risks facing the system.


Last Step
Reporting & Remediation
Once the API penetration testing finishes, we deliver a detailed report outlining the findings, their potential impact, their POC, and clear recommendations for fixing them. We also offer support during the remediation process and can retest to ensure that all issues have been properly addressed.


Our security assurance is not based on a one-size-fits-all solution.
What Makes Us Different?
Every security assessment ay CyberCovert follows a thorough process to ensure optimal results.
We specialize in uncovering API vulnerabilities through a combination of automated tools and expert manual testing.
Our methodology adheres to industry standards such as the OWASP API Security Top 10, ensuring comprehensive coverage of potential threats. We provide clear, actionable reports with prioritized remediation steps, enabling your team to address issues promptly and effectively. Our approach focuses on identifying issues like broken authentication, improper authorization, and data exposure that are often overlooked by standard testing methods.

We tailor every solution around your feedback, building trust and lasting loyalty

INDUSTRY CERTIFICATIONS
Our industry recoginzed credentials validate expertise which enhance our performance in delivering you quality work

DIVERSE INDUSTRY EXPERIENCE
From banking to healthcare to payment processors, our cross‑sector insights drive context‑driven security strategies

TAILORED SECURITY SOLUTIONS
Your business, your security—customized solutions for your unique needs

Reach Out Now
Let's Secure Your API
We can help you in staying protected.
Get In Touch
Share Your Requirements: CyberCovert Loves To Help You!
At CyberCovert, we understand the unique cybersecurity challenges facing your business, from evolving threat landscapes to stringent compliance demands.
Whether you need a API penetration test or any other assessment, share your requirements with our certified experts, and we’ll tailor a customized plan to start API penetration testing for you.

Have Any Doubt?
Frequently Asked Questions
API penetration testing is on focused on identifying vulnerabilities within application programming interfaces (APIs). It performs a series of real-world attacks to uncover flaws such as broken authentication, insecure endpoints, data exposure, and business logic issues that could be exploited by attackers.
APIs are a critical part of modern applications and often serve as gateways to sensitive data and services. If left unsecured, they become prime targets for attackers. API penetration testing helps detect weaknesses early, prevents data breaches, and ensures compliance with security standards like OWASP API Security Top 10.
Penetration testing can be performed on RESTful APIs, SOAP APIs, GraphQL APIs, and other web service architectures. Whether your APIs are public, private, or third-party integrated, they should be tested regularly to ensure they are secure against evolving threats.
Common vulnerabilities in APIs include broken object-level authorization (BOLA), excessive data exposure, lack of rate limiting, insecure authentication mechanisms, improper error handling, and injection flaws such as SQL or command injection.
While web application pentesting focuses on user interfaces and application logic, API testing targets the communication layers behind the scenes. API testing involves analyzing request/response patterns, authentication tokens, endpoint behaviors, and how APIs handle input and enforce access control.
API penetration testing follows established methodologies such as the OWASP API Security Testing Guide and NIST standards. The process typically includes reconnaissance, endpoint enumeration, authentication testing, fuzzing, exploitation, and reporting with remediation advice.
To perform an effective API penetration test, testers usually need API documentation (such as Swagger or Postman collections), authentication credentials (API keys, tokens), endpoint URLs, user roles, and details about the expected functionality and business logic.
Yes, authentication and authorization are critical focus areas during API penetration testing. We evaluate whether users can bypass login mechanisms, escalate privileges, or access data or functions beyond their intended permissions.
The duration of an API pentest depends on the number of endpoints and the complexity of business logic. A typical test may take 5 to 10 business days for small to mid-sized APIs, while larger systems with dozens of endpoints may require several weeks.
API penetration testing costs vary based on scope, number of endpoints, and test depth. Prices typically starts from $300. Comprehensive testing includes manual analysis, exploitation, and a detailed report with actionable recommendations.
Once the API pentest completes, you will receive a detailed report including an executive summary, technical findings with risk ratings, reproduction steps, impact analysis, remediation guidance and retest options to confirm fixes.
It’s recommended to test APIs annually or whenever significant changes are made—such as adding new endpoints, integrating third-party services, or updating authentication methods. Regular testing helps maintain security as your API evolves.